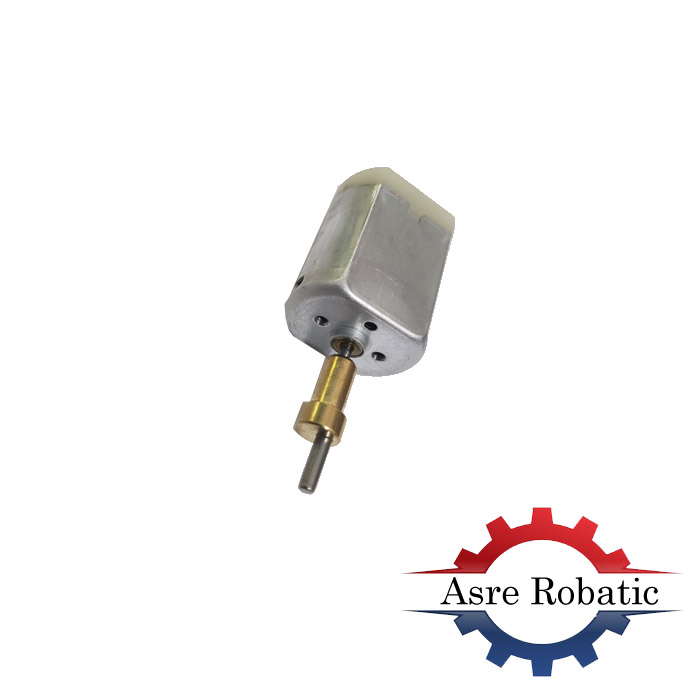
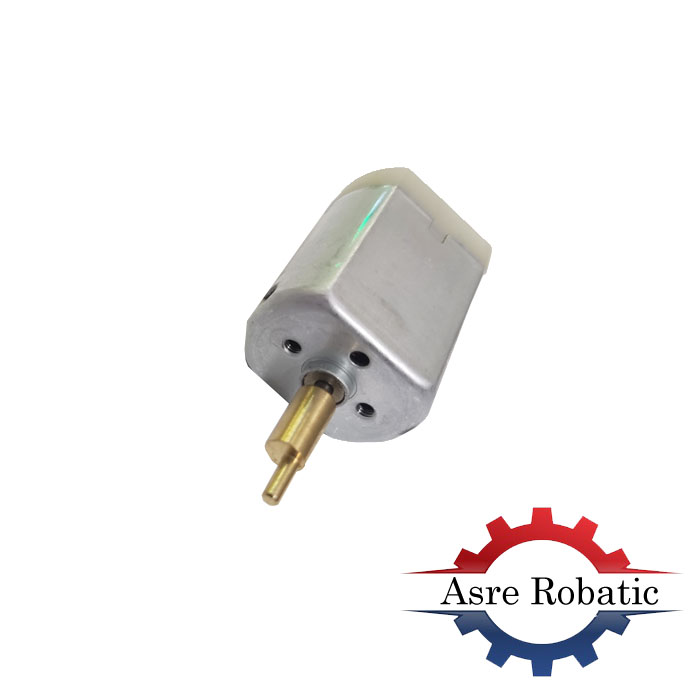



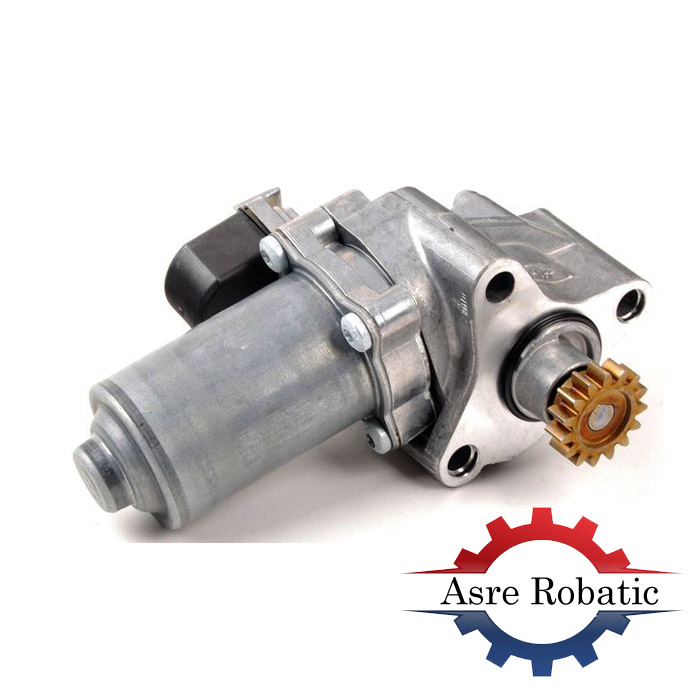
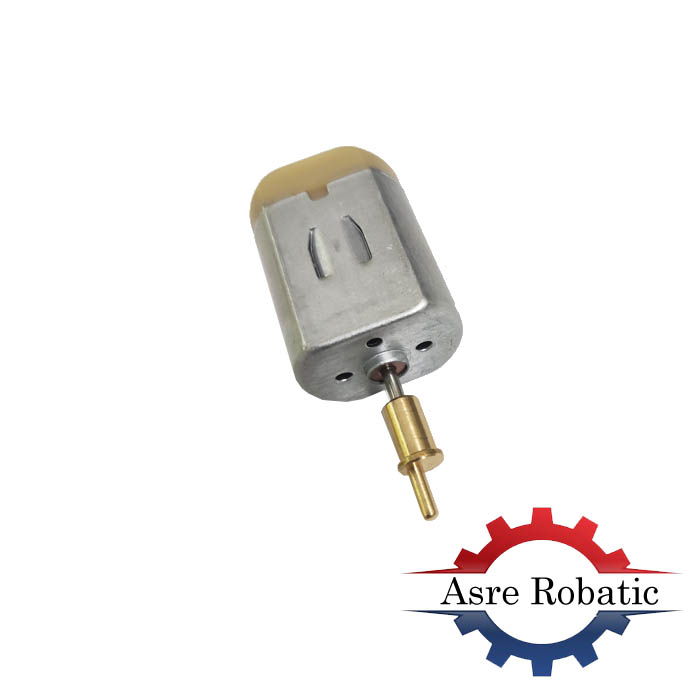

موتور DC
موتور DC
موتور DC گیربکسدار
موتور DC گیربکسدار
موتور DC گیربکسدار
موتور DC گیربکسدار
موتور DC
موتور DC گیربکسدار
چین
چین
آلمان
چین
چین
آلمان
چین
چین
3.7 V
3V
12V
12V
12V
12V
3V
12V
–
–
10Rpm
16Rpm
102Rpm
–
45Rpm
0.1A
0.1A
2.8A
0.75A
1.4A
26A
0.1A
1.4A
–
–
200 Kg/Cm
10K/gr
155Kg/Cm
–
2.5K/gr
24MM
16MM
20MM
25MM
31MM
18MM
6MM
3MM
2MM
12MM
8MM
10MM
3MM
4MM
31MM
31MM
31MM
24MM
24MM
24MM
80gr
80gr
–
–
–
1530gr
80gr
110gr
135MM
185MM
40MM
180MM
32MM, 46MM
–
33MM
جریان آب:2-3 لیتر بر دقیقه
پرتاب آب:3 متر
ارتفاع مکش:2 متر
6MM
طول 95mm-عرض 47mm-ارتفاع 36mm

